CVE and NVD CVSS Score Enhancements - Upcoming Data Changes
On November 14th, Snyk will roll out a change that will broaden Snyk Open Source vulnerabilities granularity to support CVSS vectors assigned by NVD, to support additional compliance workflows.
Background on Snyk IDs and CVE IDs:
For each new vulnerability, Snyk assigns a unique Snyk Identifier (SNYK-ID) and CVSS vector (which translates to score and severity)
This allows Snyk:
To publish new vulnerabilities faster, even before they have an officially assigned CVE ID.
To represent the issue in a single, specific package, therefore providing highly accurate information. A CVE ID, on the other hand, represents the vulnerability as a whole security issue and can be associated with multiple affected packages.
A CVE ID, on the other hand, represents the vulnerability as a whole security issue and can be associated with multiple affected packages.
In rare cases, Snyk’s Security Analysts assign multiple CVE IDs to one SNYK-ID. This happens in cases where there is very high similarity or duplicates between multiple CVEs.
Details about the change:
Starting November 14th, cases with multiple CVEs and different NVD CVSS vectors will be separated into multiple advisories (multiple Snyk-IDs), one per CVE. These cases amount to less than 0.6% of Snyk’s vulnerabilities.
This will provide customers with increased vulnerability granularity and ensure compatibility with NVD-provided CVSS vectors.
Snyk’s hand-curated CVSS is recommended for accurate and timely analysis, while NVD CVSS is useful for compliance-based needs, like FedRAMP reports.
To create a report of the vulnerabilities with the NVD CVSS Score: Click on Reports → Modify Columns → and select NVD Severity and NVD Score.
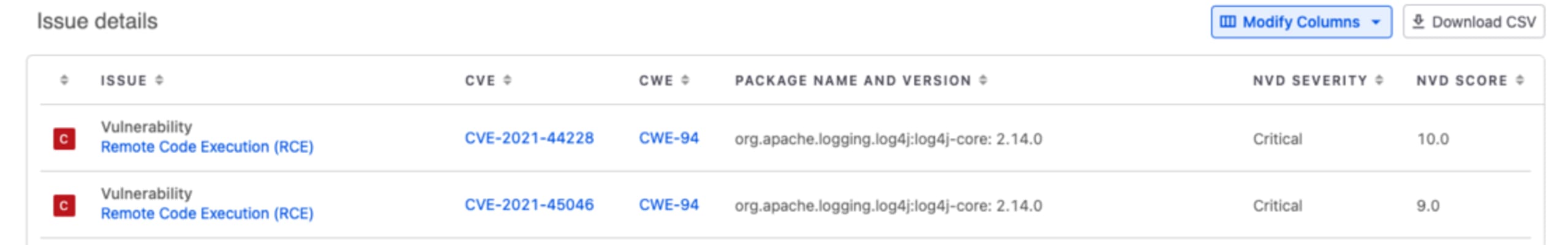
Important notes:
The number of issues you see might increase. This is due to the change in issue representation to consider NVD CVSS vectors as an independent issue factor.
After this change, in the rare cases in which multiple CVE IDs are associated with one SNYK-ID, the NVD CVSS vector provided will be relevant for both CVE IDs. A retest, a manual test, or a scheduled scan for monitored Projects, is needed to see the changes.
Although the overall number of issues (Snyk Open Source) might increase due to the broadening of the granularity to include NVD and CVSS vectors, these issues can be solved with the same fix.
If a new advisory was created from an ignored issue, it will still appear in the Project. If not relevant, the new issue will need to be ignored as well. This is because the new advisory has a different NVD CVSS score, and Snyk cannot assume it is irrelevant to your Project.
The Snyk CVSS will remain similar between the advisories.
The related CVE, which the advisory was separated from, will be included in the advisory details.